SSH?
Today, security plays an important role on the internet. That’s why the SSH security procedure is firmly anchored in the TCP / IP protocol stack. In fact, the SSH protocol makes it possible to establish a secure connection between two computers. This protocol has been around since 1995 and has been revised several times. It is made to replace the Telnet protocol that is no longer used.
With this self-study you can know what the SSH protocol is but also to understand how it works and why you may need this protocol.
What is SSH?
SSH is a network protocol for fully secure communication between two computers. When a user talks about SSH usage, it refers to using an SSH client to connect to a remote server. Whether you use Linux, MacO & # 39; s or Windows, you can use this protocol to securely connect to a server. Once connected in SSH, you can execute commands on the remote server.
Why use SSH?
As mentioned above, the With SSH you can establish a secure and direct connection within a potentially unsecured network. This is indeed necessary to protect the data stream that you send to the external server.
The SSH protocol also guarantees that the data cannot be changed by third parties before they reach their destination.
SSH can do many things such as:
- Management of locally inaccessible servers;
- Secure transfer of files;
- Secure creation of backups
- Connection between two computers with end-to-end encryption.
How does SSH work?
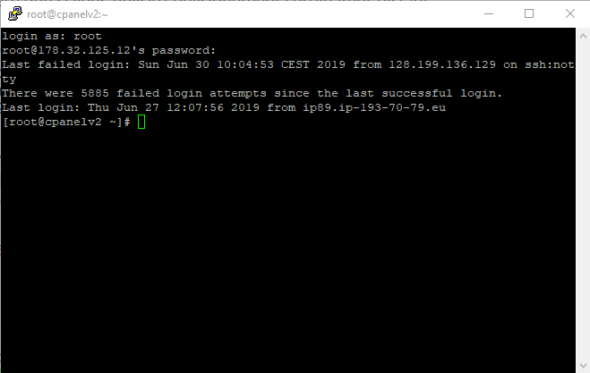
If you use Windows, you can use software such as Putty to connect to your server via SSH. For Linux and MacOS users, however, you must follow the procedure below after accessing the Terminal:
ssh {user} @ {host}
The SSH command consists of:
- {Users}: Represents the account that you want to access.
- {B}: refers to the server that you want to connect to.
After the command has been entered on your terminal, press the “entry“. You will be asked to enter your password. When entering the SSH login password, nothing is displayed on the screen. This is completely normal. After the last one is encrypted, press the”entry“From your keyboard.
What are the different SSH coding techniques?
In comparison with Telnet without coding, thanks to the connection through SSH you can ensure a secure transfer information between the host (the external server) and the client (your computer). There are 3 different types of coding that are:
- Symmetrical coding
- Asymmetrical coding
- hashing
Symmetrical coding
the symmetrical coding is a form of encryption in which a secret key is used immediately for encoding and decoding a message, both by the client and by the host. Indeed, all people with the key can decrypt the message sent. Symmetric coding is one of the simplest methods to understand. With this method we use a key (a secret password) to encrypt the message. The same key is used to decrypt the message.
Therefore it is necessary that the person who encrypts and the person who will decrypt the message knows the secret key.
As noted, symmetrical encryption is therefore very powerful, but it has a big mistake: sharing secret keys. It is indeed necessary to share the encryption key. In many cases, this key is clearly shared, which can be a safety issue.
However, it is quite possible to encrypt this key when it is sent. This is the asymmetrical encryption method.
Asymmetrical coding
Asymmetrical encryption functions for him of two separate and functional keys of pairs. This is the public key and the private key.
So there are two keys:
- public key: this key is used for encryption.
- private key: this key is used to decrypt.
With this type of encryption, we can only decrypt a message if we know the private key. We speak of asymmetric encryption to the extent that it is necessary to have two different keys. Moreover, this type of coding is more secure
The SSH connection uses both types of digits: asymmetrical and symmetrical as follows:
- In the first instance we use asymmetric encryption to discretely exchange a secret key of symmetrical encryption
- Once connected, only symmetrical coding is used to code the exchanges.
hash
One-way hashing is another form of cryptography that is used in Secure Shell connections. This is completely different from the two types of coding seen above. Indeed, this form of coding is not intended to be decoded.
It is easy to generate a cryptographic hash based on a given input, but you cannot generate the input from the hash. This means that if a client has the correct input, he can generate the cryptographic hash and compare its value to check if it has the correct input.
What are the different steps of SSH encryption?
With regard to FTP connections, SSH uses the client-server model to enable identification and coding of the exchanged data. The latter connects to port 22, the default port, although you can change this port if necessary. The connection must be made in two steps:
- Both systems must first agree on the coding standards to be used to protect future communications.
- The user must authenticate
Although passwords are encrypted, it is not recommended to verify with this method. Indeed, many robots can try to connect with a simple password and gain access to your account. It is therefore preferable to connect via asymmetric encryption that offers better security.
Set up email on iPhone and Mac
conclusion
If you understand how SSH works, you can better understand the security aspects of this technology when you subscribe to a VPS server. Thanks to this article you also know why Telnet was abandoned in favor of SSH. Feel free to share your encryption experience with us in response ?



